Is there a command which can elevate the Command Prompt in place?
Solution 1:
TL;DR - The only option is to spawn another process. (A new cmd.exe.) In the case of the Command Prompt, starting a new instance with an access token that has higher permissions will always result in a new window being created.
It's not possible to grant additional permissions to an already running process.
When a user with administrative rights logs into a Windows machine with User Account Control (UAC) enabled, two separate access tokens are created:
- One with full administrator access, and
- A second "filtered token" with standard user access
At the time a process (e.g. CMD.EXE) is created, it is assigned one of these two access tokens. If the process is run "elevated" as Administrator, the unfiltered access token is used. If the process is not granted admin rights, the filtered, standard user token is used.
Once a process has been created it is not possible to replace its access token.1 In this MSDN Application Security for Windows Desktop thread, a poster identifying himself as a member of the Windows Kernel Team states:
The NT kernel was never intended to allow token switching once a process started running. This is because handles, etc. may have been opened in an old security context, inflight operations may use inconsistent security contexts, etc. As such, it typically does not make sense to switch a process' token once it has begun execution. However, this was not enforced until Vista. [emphasis mine] (Source thanks to @Ben N)
Note: User Account Control was introduced with the release of Windows Vista.
This Super User answer cites two additional sources confirming the same:
-
The devzest.com blog post Programming Elevated Privilege/UAC:
Code can only be elevated at process level when startup, which means that a running process cannot be elevated. In order to elevate an existing application, a new instance of the application process must be created...
-
The techtarget.com article How to elevate programs' privileges correctly using Vista's UAC:
Programs can't be elevated once they've already been launched...
Therefore it's simply not possible to elevate Command Prompt or any other process in-place. The only option is to spawn another process with a new access token (which can be another instance of the original process if desired). In the case of the Command Prompt, starting a new instance with an access token that has higher permissions will always result in a new window being created, and if UAC prompts are enabled on the system, they will be triggered as well.
1You can adjust the privileges in an existing access token with the AdjustTokenPrivileges function, but according to MSDN:
The AdjustTokenPrivileges function cannot add new privileges to the access token. It can only enable or disable the token's existing privileges.
Solution 2:
While I am an enthusiastic user of TCC-LE, there is a solution which does not need any new programs:-
- Start
cmdas administrator. - This should start you in
%SystemRoot%\system32\- if not,cdthere. -
copy cmd.exe cmdadmin.exe(or any name you choose, such assu.exe). - Now run Explorer and find
cmdadmin.exe. - Right-click and select Properties.
- In the Compatibility tab select run as admin (or set it for all users).
Now cmdadmin is your su or sudo: you can start it without parameters to give you a shell with administrative privileges, or you can run it with /c to execute a single command in this mode. Depending on your policies, you may or may not be prompted for confirmation.
Note that this will always open a new window (as does the TCC solution start /elevated ...): for a GUI application this is expected, but for a command-line program, you may want to use /k instead of /c, to give you a chance to see the output; or you could run via a batch file (sudo.cmd perhaps?) which concatenates & pause to the end of your run string.
In either case it's not quite the same as su or sudo, but it's the closest you'll get. By setting the windows layout manually, the new window can be created directly below and abutting the original.
Solution 3:
Is there a command which can elevate the Command Prompt in place?
There is a rather inconvenient way:
powershell -Command "Start-Process 'cmd.exe' -Verb runAs"
There were better ways but Microsoft closed them. Of course, you can always roll up your sleeves and write your own script equivalent of sudo with the source code I just gave you.
In other words, it should not spawn a new window or display UAC prompts.
Blasphemy! Burn him in the stake! ;) Joke aside, no. There isn't. That would be a bug and a security vulnerability. Microsoft made an explicit effort to ensure that the elevated and the standard process have as little in common as possible.
Smart kids who are thinking about two back-ends (one standard and one elevated) and one graphical front-end for both, should read about Session 0 Isolation.
Solution 4:
It shouldn't be possible to elevate skipping the UAC, otherwise it violates a windows security principle.
But there are tools that allows this. Like gsudo, a sudo for windows that allows to elevate the command prompt in place. I am the author.
It shows a UAC window for the first elevation. If you gsudo again before the elevated gsudo timeouts, it wont ask for UAC again.
Features
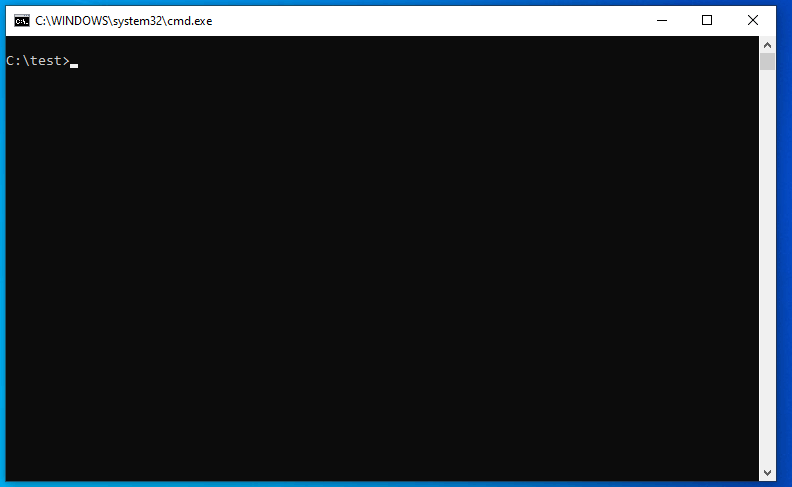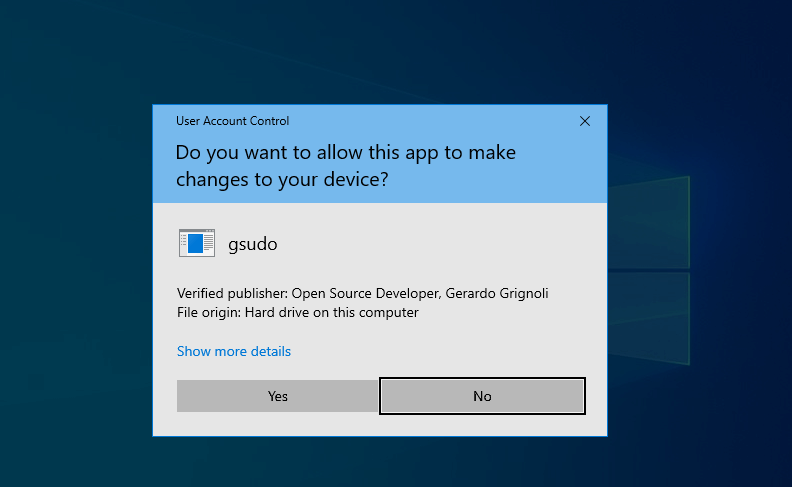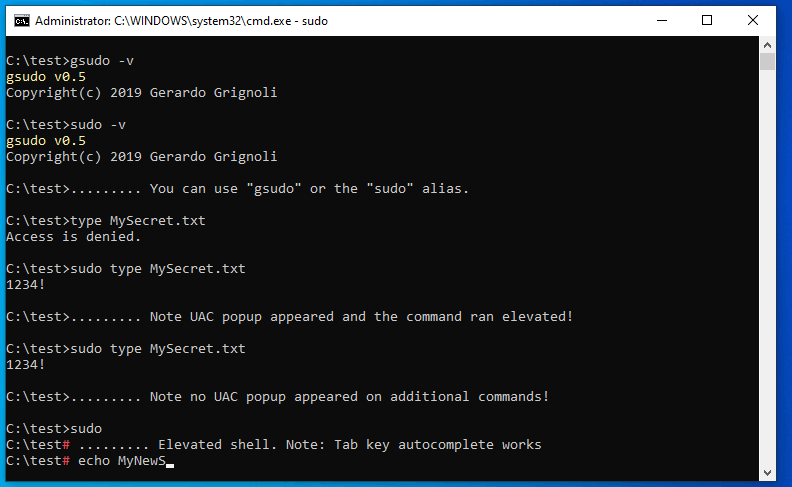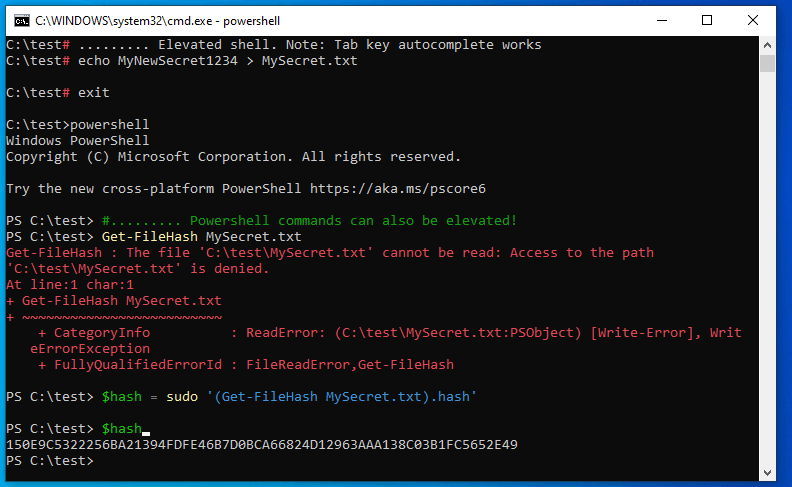
- Elevated commands are shown in the user-level console, as
*nix sudodoes, instead of opening the command in a new window. - Credentials cache: If
gsudois invoked several times within minutes it only shows the UAC pop-up once. - Suport for CMD commands:
gsudo md folder(no need to use the longer formgsudo cmd.exe /c md folder - Suport for PowerShell commands if invoked from a PS shell.
- Scripting:
-
gsudocan be used on scripts that requires to elevate one or more commands. (the UAC popup will appear once). - Outputs and exit codes of the elevated commands can be interpreted: E.g. StdOutbound can be piped or captured (
gsudo dir | findstr /c:"bytes free" > FreeSpace.txt) and exit codes too ('%errorlevel%)). - If
gsudois invoked (with params) from an already elevated console it will just run the commands. So if you invoke a script that usesgsudofrom an already elevated console, it will also work. The UAC popup would not appear.
-
Installation
- Install via Scoop:
scoop install gsudo - Install via Chocolatey:
choco install gsudo - Or:
PowerShell -Command "Set-ExecutionPolicy RemoteSigned -scope Process; iwr -useb https://raw.githubusercontent.com/gerardog/gsudo/master/installgsudo.ps1 | iex"
See it in action:
Github Project https://github.com/gerardog/gsudo