WireGuard allow access to single service on network
Solution 1:
To answer your questions briefly:
- Yes
- The
INPUT/OUTPUTchains are used for connections to/from local sockets on all interfaces (lo,eth0,wg0, etc). Usually you don't want to block everything outbound by default because you'll end up spending time troubleshooting things you normally take for granted (DNS, DHCP, NTP, misc processes using loopback connections, etc) - Yes. Usually it's fine to just allow all
RELATED,ESTABLISHEDwithout any additional conditions (if you already allowed a connection through one way, symmetrical responses going back the other way should be fine too) - Yes
- Yes
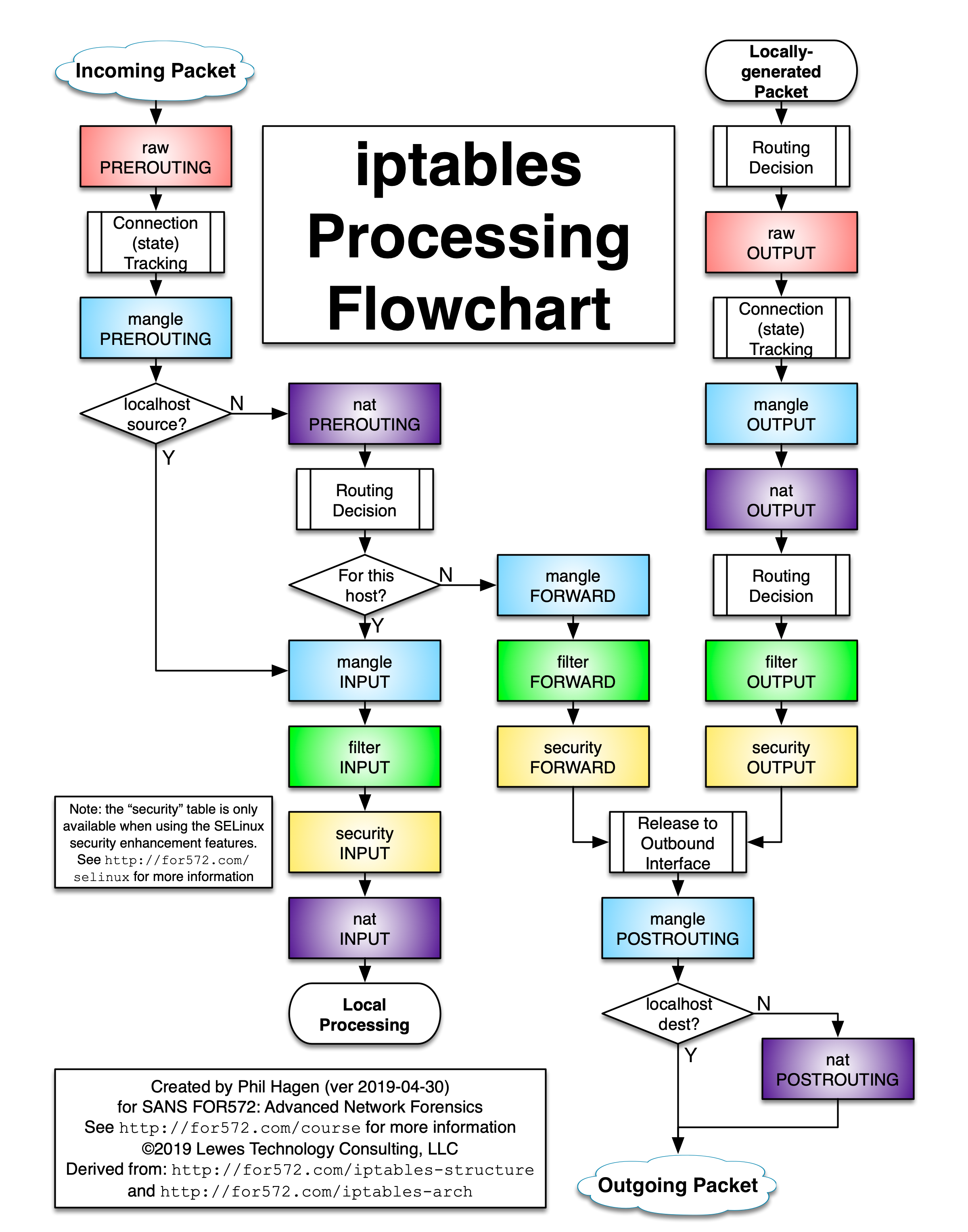
I think this iptables processing flowchart will also help you better understand how this works:
This is how I would write your rules:
iptables -P INPUT DROP
iptables -P FORWARD DROP
iptables -P OUTPUT ACCEPT
# INPUT chain of filter table:
# drop known bad packets
iptables -A INPUT -m state --state INVALID -j DROP
# accept responses to established connections
iptables -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
# accept ICMP packets
iptables -A INPUT -p icmp -J ACCEPT
# accept loopback connections
iptables -A INPUT -i lo -J ACCEPT
# accept connections to WireGuard listen port
iptables -A INPUT -p udp --dport 51820 -J ACCEPT
# FORWARD chain of filter table:
# drop known bad packets
iptables -A FORWARD -m state --state INVALID -j DROP
# forward responses to established connections
iptables -A FORWARD -m state --state RELATED,ESTABLISHED -j ACCEPT
# forward ICMP packets from WireGuard network to NAS
iptables -A FORWARD -i wg0 -d 192.168.178.23 -p icmp -J ACCEPT
# forward SMB connections from WireGuard network to NAS
iptables -A FORWARD -i wg0 -d 192.168.178.23 -p tcp --dport 445 -J ACCEPT
# POSTROUTING chain of nat table:
# masquerade all packets forwarded to LAN
iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE